
-
Products
-
Solutions
-
Use Cases
- Plan Cloud Migration Application Dependency Mapping Disaster Recovery
- Resolve Full Stack Observability Kubernetes Observability Multi-Cloud Observability Infrastructure Performance Monitoring Application Performance Monitoring Network Performance Monitoring VDI Troubleshooting Log Analysis AWS, Azure and Google Cloud Monitoring Nutanix & HCI Observability Storage Monitoring Database Monitoring SaaS Monitoring Physical Server Monitoring
- Optimize End-user Experience Monitoring Capacity Planning Data Center Consolidation
- Secure Threat Detection and Analysis Application Anomaly Detection Lateral East-West Movement Analysis Microsegmentation Monitoring and Planning
-
Industry
-
Role
-
-
Resources
End-to-end & Unified Observability, Troubleshooting & AIOps Remediations
-
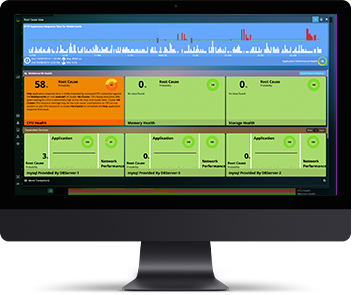 Multi-Cloud Observability & TroubleshootingAccurate 360-degree Observability & AIOPS Remediation for Application, Infrastructure, Network & VDI UsersLearn More
Multi-Cloud Observability & TroubleshootingAccurate 360-degree Observability & AIOPS Remediation for Application, Infrastructure, Network & VDI UsersLearn More -
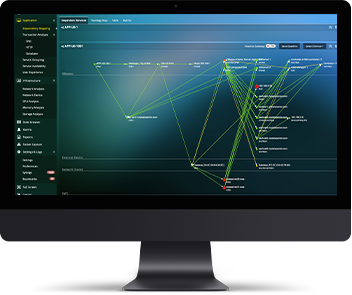 Application Dependency MappingAutomated & Dynamic Application/Infrastructure Topology Tracing & MappingLearn More
Application Dependency MappingAutomated & Dynamic Application/Infrastructure Topology Tracing & MappingLearn More -
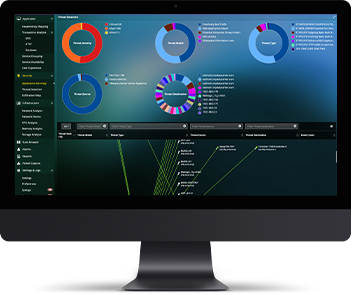 App-Centric Cyber Threat ProtectionApplication Anomaly & East-West Network Traffic-based Security ProtectionLearn More
App-Centric Cyber Threat ProtectionApplication Anomaly & East-West Network Traffic-based Security ProtectionLearn More
“Uila uObserve™ Incident Savings Calculator”
Calculate the Impact of Outages/Downtime on your Organization and how much you can SAVE with Uila
Savings with Uila uObserve™ for IT Operations (Server, Network & Desktop) teams
-
0 Users Realized ROI in 3-6 months -
0 Users gave Uila a "Very Satisfied" rating and above -
0 % Reduction in Time for Cloud Pre-Migration Assessments -
0 Less time spent in Troubleshooting -
0 Reduction of Unplanned Downtime
Why do IT teams rely on Uila uObserve™?
- Accelerate Incident Resolution
- Rapid Time to Value & low TCO
- Maximize IT Productivity with Silo Elimination
- Maintain Revenue & Reputation
- Uila as a "Team Extension" with Technical Engineer Support
- Optimize IT Spending
- Nullify Legal & Privacy Issues
- Reduce Service Outages
What users say about Uila ("we-la") uObserve™?

“Uila provides me with the insights I need to keep my business running smoothly”
- Reviewer role
IT Director -





“The software is really great to get a quick glance at the state of all of our systems”
- Reviewer role
System Administrator -





Read our reviews on
Gartner Capterra

“Sonar Screen-style Heat Maps and Analysis Tools pinpoint Virtual Infrastructure Problem Areas”
- Reviewer role
Infrastructure Engineer -





“Easy to Implement and Provided Priceless Value Almost Immediately”
- Reviewer role
Director - IT Operations -





Read our reviews on
Gartner Peer Insights
Customer Success Stories
-
 Download"We have been able to solve all the complaints that have been directed towards my team for infrastructure driven application complaints.”Mark Martinez
Download"We have been able to solve all the complaints that have been directed towards my team for infrastructure driven application complaints.”Mark Martinez
IT Director, Harris County -
 Download"Whenever there’s a performance issue now, we can go in to Uila and it’s much easier to find out why.”James Oryszczyn
Download"Whenever there’s a performance issue now, we can go in to Uila and it’s much easier to find out why.”James Oryszczyn
Director of Security & Network Services, Quarles & Brady -
 Download"Uila has given us the capabilities to proactively tune our applications & determine the optimal system upgrades”Mike Johnson
Download"Uila has given us the capabilities to proactively tune our applications & determine the optimal system upgrades”Mike Johnson
Director of IT, The Myers-Briggs Company -
 Download"Uila's ability for virtual environment visibility is something I have not seen in any other product”Henry Mayorga
Download"Uila's ability for virtual environment visibility is something I have not seen in any other product”Henry Mayorga
CSO and VP of Infrastructure, Baron Capital
-
 Application Dependency MappingWatch Video
Application Dependency MappingWatch Video -
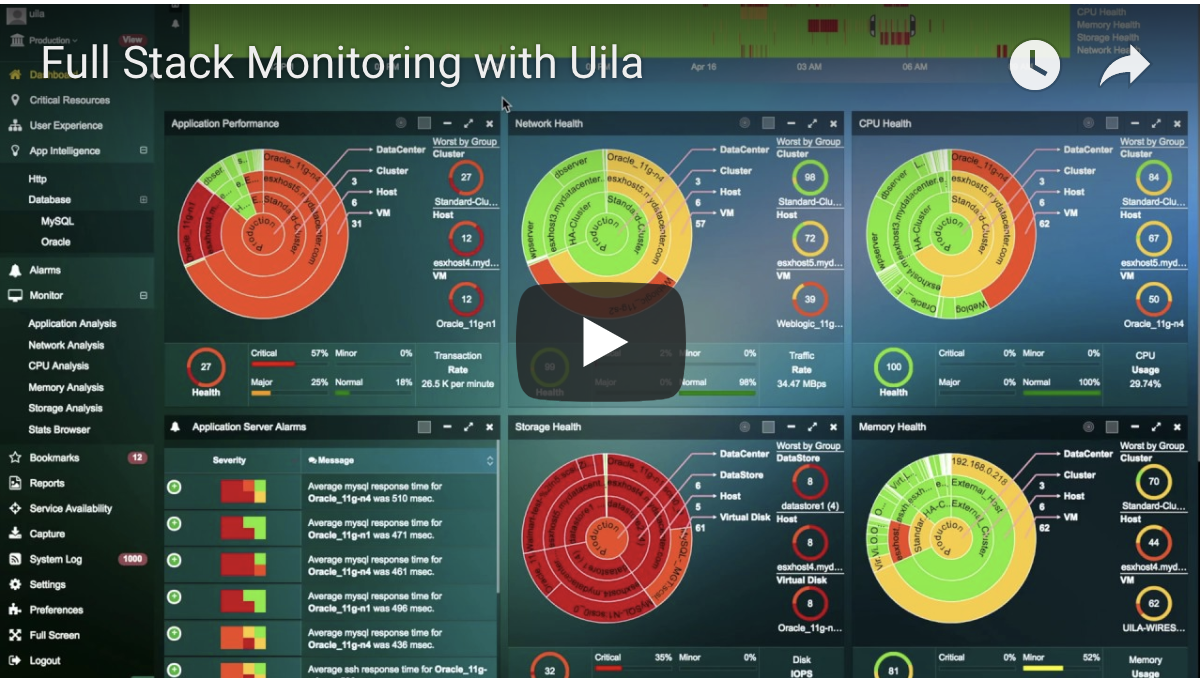 Full-Stack ObservabilityWatch Video
Full-Stack ObservabilityWatch Video -
 Network Device MonitoringWatch Video
Network Device MonitoringWatch Video -
 VDI/EUC Observability & TroubleshootingWatch Video
VDI/EUC Observability & TroubleshootingWatch Video



