Proactively Detect Advanced Malicious Threats in Real-Time for Data Center and Cloud Workloads
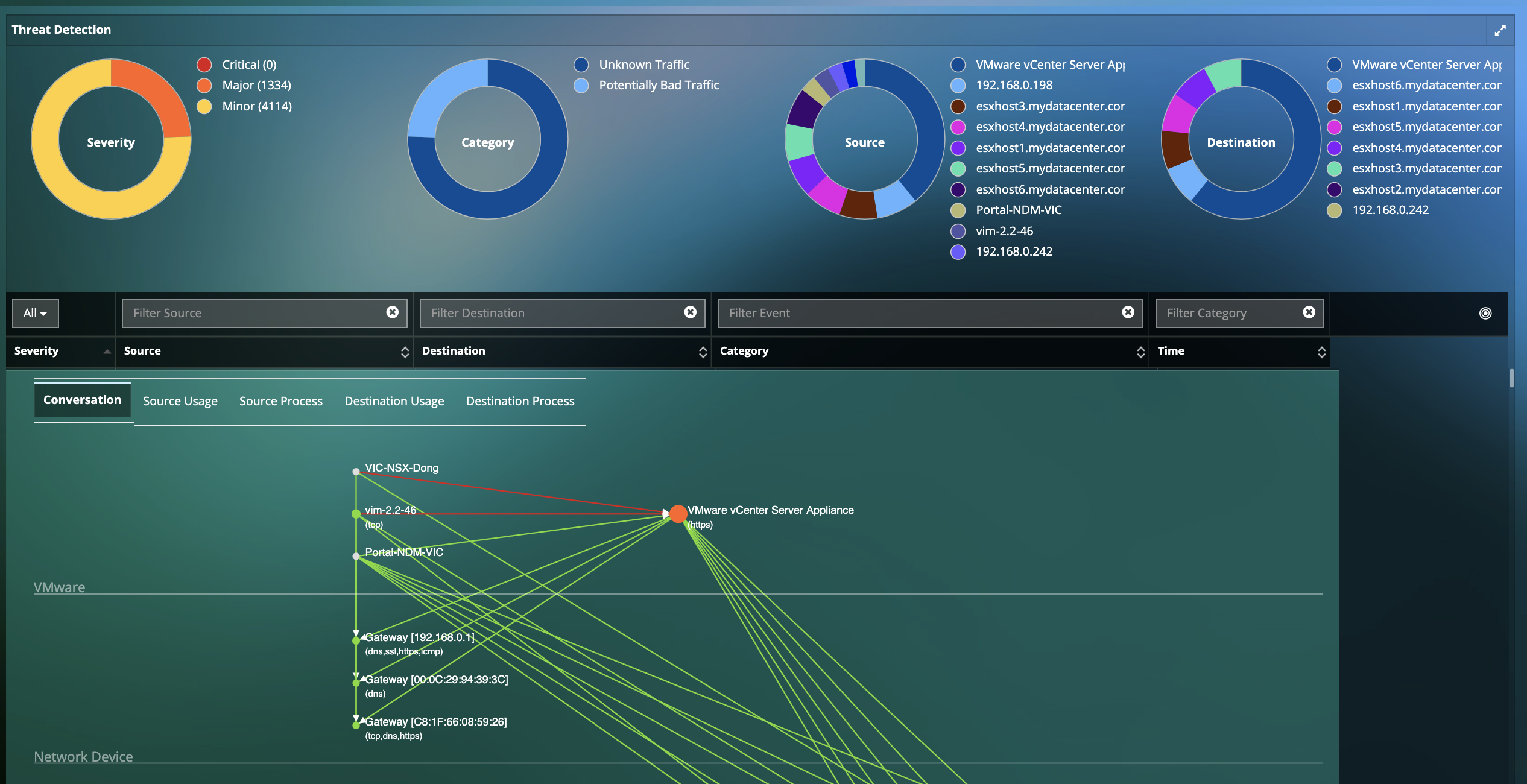
- Real-time Detection for thousands of Advanced and Persistent threats including Malware, Exploit Kits, Webshells, Port Scans, SMB Probes, Information Leakages, Obfuscation, OS fingerprinting, and many more. :
- Latest threat rules support and updates from the largest group dedicated to advances in the network security industry.
- Insights into historical context of the origins of threats, even across cloud boundaries.
- Unique insights into Dependencies and Infrastructure associated with threat.
- Rich Threat Intelligence with detailed Information on impact, systems affected, CVE information, corrective actions, etc.
Automate SecOps with Intelligent Remediations
- AIOps to streamline any cyber threat and vulnerability troubleshooting and reduce MTTR with remediation actions across the infrastructure. Intelligent Alert-based triggers and Manual triggers provide complete control in proactively preventing issues as well as streamlining problem resolution.
- Increase Security IT team efficiency and agility by automating repetitive tasks and focusings on issues that matter by reducing alert noise.
- Based on Uila’s full-stack ML-based Root-cause analysis that rapidly isolates issues. Actions include Power off VMs, Suspend VMs, Reset VMs, Power On VMs, logging off VDI users, Updating VMware tools, Restart Guest OS, Kill a process running on a VDI desktop, etc.
Deep Insights into Current as well as Potential Compromised Assets
- Monitor Dependencies, Process and Infrastructure (CPU cores, CPU capacity, Memory, Network Traffic) for Compromised systems.
- Insights into future compromized assets with unique Dependency Mapping visibility.
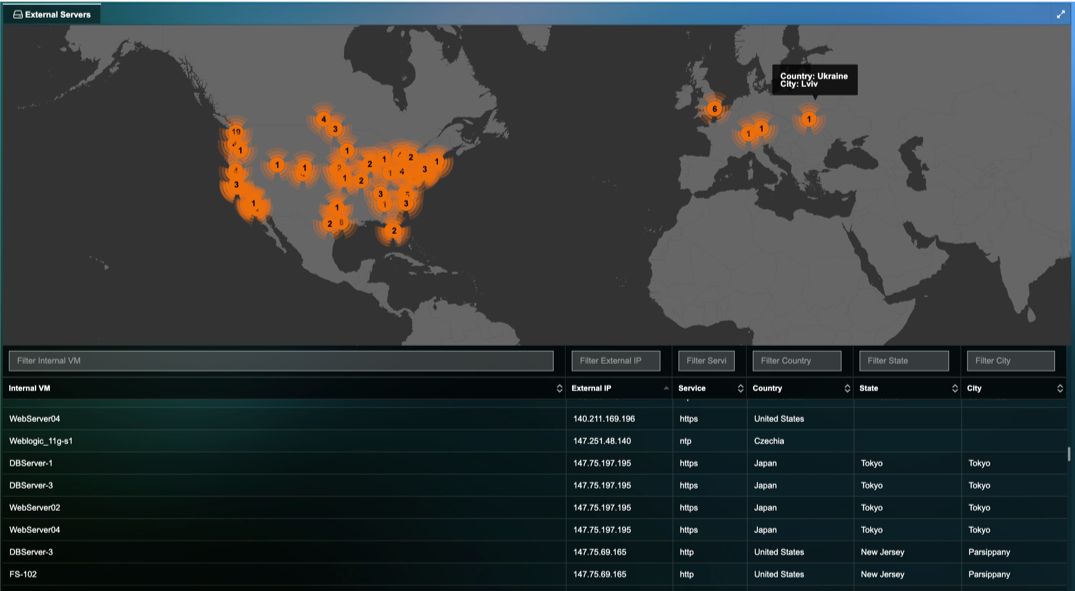
Manage Unauthorized Data Exfiltration
- Reduce Risk associated with outbound connections with immediate visibility into Traffic Exfiltration from your deployment to unauthorized or malicious locations.
- Visualize Outbound traffic details on a world map including Internal VM details, Destination IP, Destination Server location, Application/Service for the outbound traffic, etc.
- Conclusive chain of evidence with Application Transaction information.
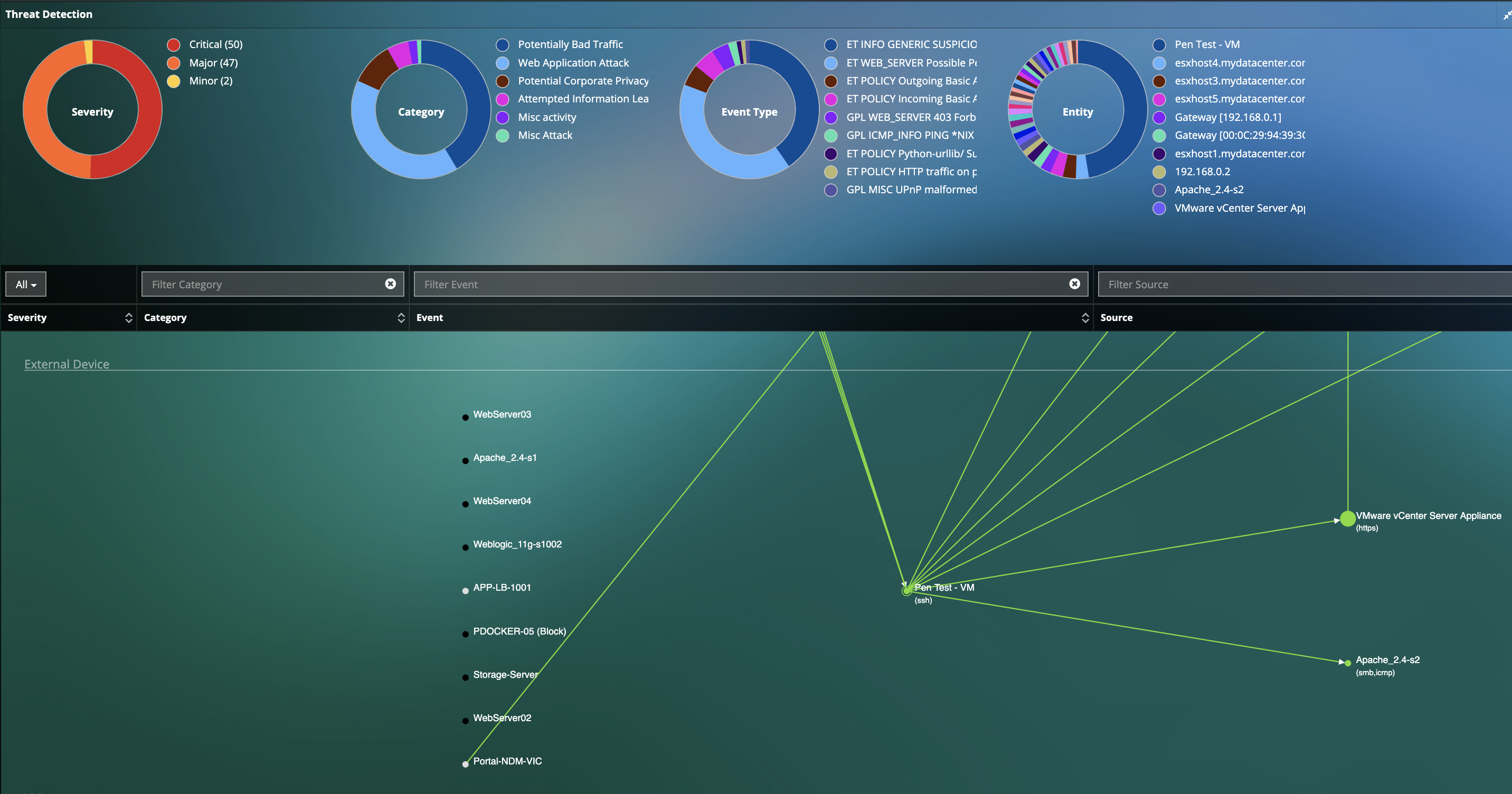
Conclusive Chain of Evidence for any Threat
- Detailed forensic reconstruction to assist security defenders to determine when and how delivery of the cyber threat began.
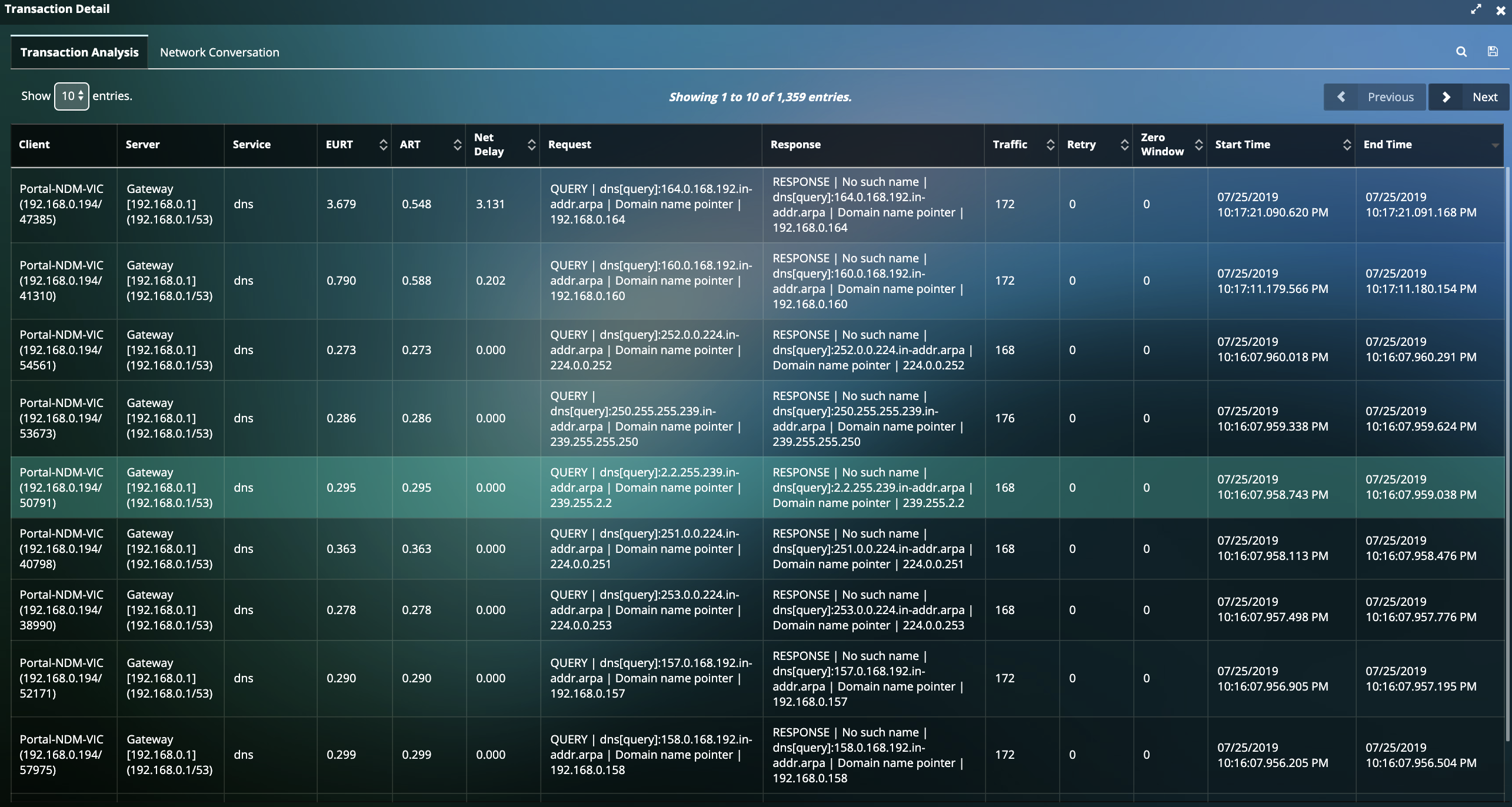
- Detailed transaction analysis at the application level to analyze time of day for the entire Hybrid environment of when cyber attack began.
- Packet Capture for forensic evidence.
Resources
-
Uila real-world use case: Identifying Malware infected VDI desktopQuick video on how Uila uObserve was used to identify a malware infected VDI desktop.
-
Cyber Threat Monitoring for the Hybrid EnterpriseQuick 3 minute video that talks about the changing Threat Landscape with attacks moving laterally within the Data Center and Cloud deployments, the importance of identifying Application Anomalous Behavior and Data exfiltration activities and finally on how you can protect your mission critical application workloads with Uila.
-
Uila's DPI Methods for Detecting Lateral MovementQuick overview on Uila's DPI methods for lateral movement detection.
-
Uila for Webshell Threat DetectionQuick brochure on how to use Uila for Webshell Threat Detection.
-
Cyber Threat Detection with UilaQuick video on how Uila can identify advanced cyber threats in your deployment.
-
Outbound Traffic Analysis with UilaQuick video on how Uila can monitor for outbound traffic from your data center resources to the Internet.
-
Uila for Cyber Threat Monitoring Solution BriefQuick solution brief on Uila's Application-centric approach to cyber threat monitoring.
Ready to begin your Monitoring Journey with Uila?
Start a 21-day Free Trial Now
Request Trial