Let’s start with a definition …
What is Shadow IT?
At its most generic and abstract, Shadow IT constitutes devices, software, and service accounts not explicitly provided or approved by the organization. More directly, what we are really talking about in this context are third-party cloud sync services (e.g., Dropbox, Google Drive, iCloud), and users bringing in their own devices such as phones and laptops. This also includes things like a rogue admin deploying new servers and using modified, unapproved configurations.
With the rise of smartphones in the late 2000s, a movement began that went through a few different naming conventions. Users discovered that they could bring in their own devices, connect them to the company network, and do whatever they wanted to with them -- without the typical desktop control and oversight they were subjected to by the organization.
This presents several problem scenarios. If you ask any network engineer what the biggest issue was at that time, it was users “looping” the network with their own routers/hubs, taking entire switches (and subsequently, entire office buildings) offline. The tools back then were also pretty lackluster, and troubleshooting would involve hours of sifting through logs manually.
So when users began connecting their own iPhones to the company network, it put excessive load on wireless networks, drove risk of confidential data leaks through the roof, and brought a whole new level of management to the helpdesk to configure each user’s device.
One part of this is related to data, while another part centers around Bring Your Own Device (BYOD) mentalities. With the various cloud sync and email services out there, it was no big deal for an end user to install a client on their workstation and sync their entire home or departmental shared drive full of confidential information, with no real audit trail, and possibly landing on a sync destination that was unencrypted. This was especially dangerous for use cases like spreadsheets in a healthcare company. It wasn’t uncommon for database exports/reports to have Personally Identifiable Information (PII) in them.
With desktops that were pre-configured and locked down, it was easy to prevent users from performing this rogue install in the first place. Times have changed.
Enter the BYOD Era
We’ve all worked in corporate environments where the computers provided to us were, shall we say … lackluster. So it was perhaps a bit more understandable when users took matters into their own hands: “Hey! If I can bring in and connect my own phone, why not my own laptop? At least it’d be faster than this hunk-o-junk IT gave me.”
And just like that …. BOOM! The era of Shadow IT was in full swing as companies began relaxing their policies. They allowed non-approved BYOD computers to connect to the network, install company software, and go on about their day with little or no oversight.
Network Security Analytics and Change Control in the Datacenter
Uila’s robust platform empowers you to eliminate concerns around Shadow IT, stay on top of changes, and stay in alignment with your organization’s business objectives. It’s not a magic switch, or a Big Red Button, but it does provide an incredible wealth of knowledge, elegantly packaged together to provide actionable information from raw data.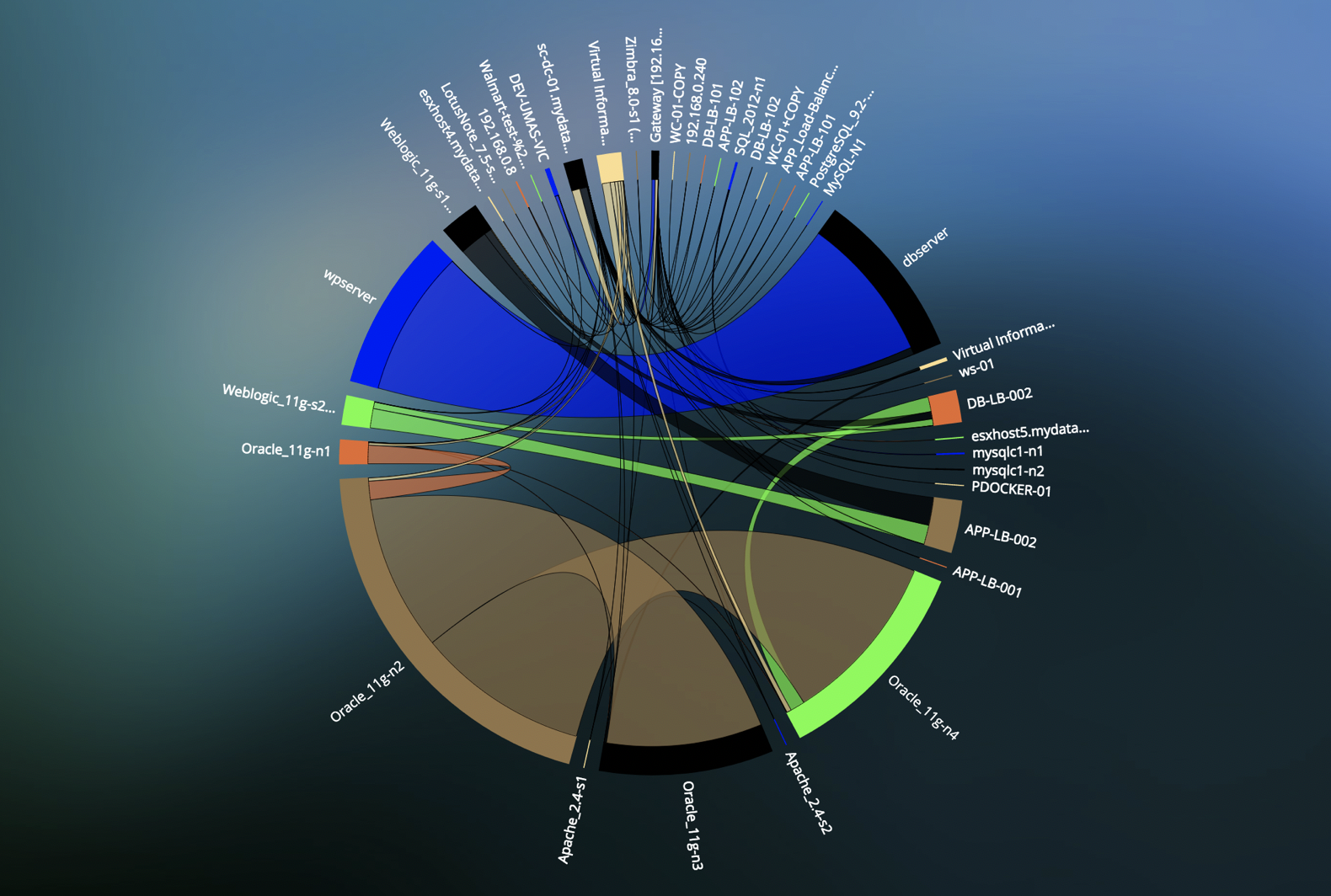
With support for change management, admins are able to manage the unpredictable evolution of ever-changing IT workloads, networks, and new technologies immediately. We can also provide your IT staff with proactive alerts when new servers or applications are being deployed when or how they shouldn’t be, as well as insights into existing misconfigurations within your infrastructure, network, and applications.
Uila provides real-time full-stack network security insights with comprehensive statistics across applications, infrastructure, and networks, including east-west traffic across VMs. We’re even able to detect abnormal patterns of connections and traffic flow that indicate a potential security threat behind the firewall. In addition, we’re also performing packet capture and deep packet inspection for forensic evidence to solve many network security challenges. We’re proud to say that Uila has the ability to identify nearly all protocols and applications responsible for IP flows, on both mobile and wired networks, in any geography.
Is it about Users or the Datacenter?
Well, frankly … BOTH! Users connect to and store their data in resources within the datacenter. File servers, shared storage arrays, and much more house all of that data, and can sometimes go years without receiving updates.
That’s why it’s imperative that you have a complete, top-down and east-west view of all traffic traversing your datacenter, to detect BYOD breaches, security issues, or anything else potentially compromising your datacenter. Uila can provide that for you.
Would you like to try an interactive demo? Click here!
Subscribe
Latest Posts
- How Data Center System Administrators Are Evolving in today's world
- Microsoft NTLM: Tips for Discontinuation
- Understanding the Importance of Deep Packet Inspection in Application Dependency Mapping
- Polyfill.io supply chain attack: Detection & Protection
- Importance of Remote End-User Experience Monitoring
- Application and Infrastructure Challenges for Utility Companies
- Troubleshooting Exchange Server Issues in Data Centers
- Importance of Application Dependency Mapping for IT Asset Inventory Control
- Navigating the Flow: Understanding East-West Network Traffic
- The imperative of full-stack observability




