Digital Transformation in the Healthcare World
-
Healthcare organizations are seeing an explosion in the amount of health data that is being generated, but IT teams supporting those organizations get overwhelmed supporting the sheer amount of data. Add to that the HIPAA compliance regulations, tight budgets and security concerns, and the job for the teams get tougher. This could lead to lower productivity levels and overall patient care getting compromised.
To improve patient care, which depends on patient experience is of utmost importance for the healthcare organizations. This includes both, supporting the medical applications accessed by the medical staff to provide that patient care, as well as the applications or network access for the patient or guest access networks. For example, here are a few applications that healthcare organizations would care about:
- Accessing patient records by medical staff
- Emergency room application access in a timely manner
- Patient admission systems
- Insurance payment systems
- Pharmacy systems
- Digital imaging and communication
- EHR that needs to be accessed immediately by the medical staff, but also archived securely based on HIPAA regulations
- VDI and Mobile access
Full Stack Observability in a Single Product
- Align business and IT Operations goals in a single product with application visibility and correlated network, compute and storage insights to solve problems before end-user impact.
- Reduce time in War room conversations and instead focus on business acceleration projects.
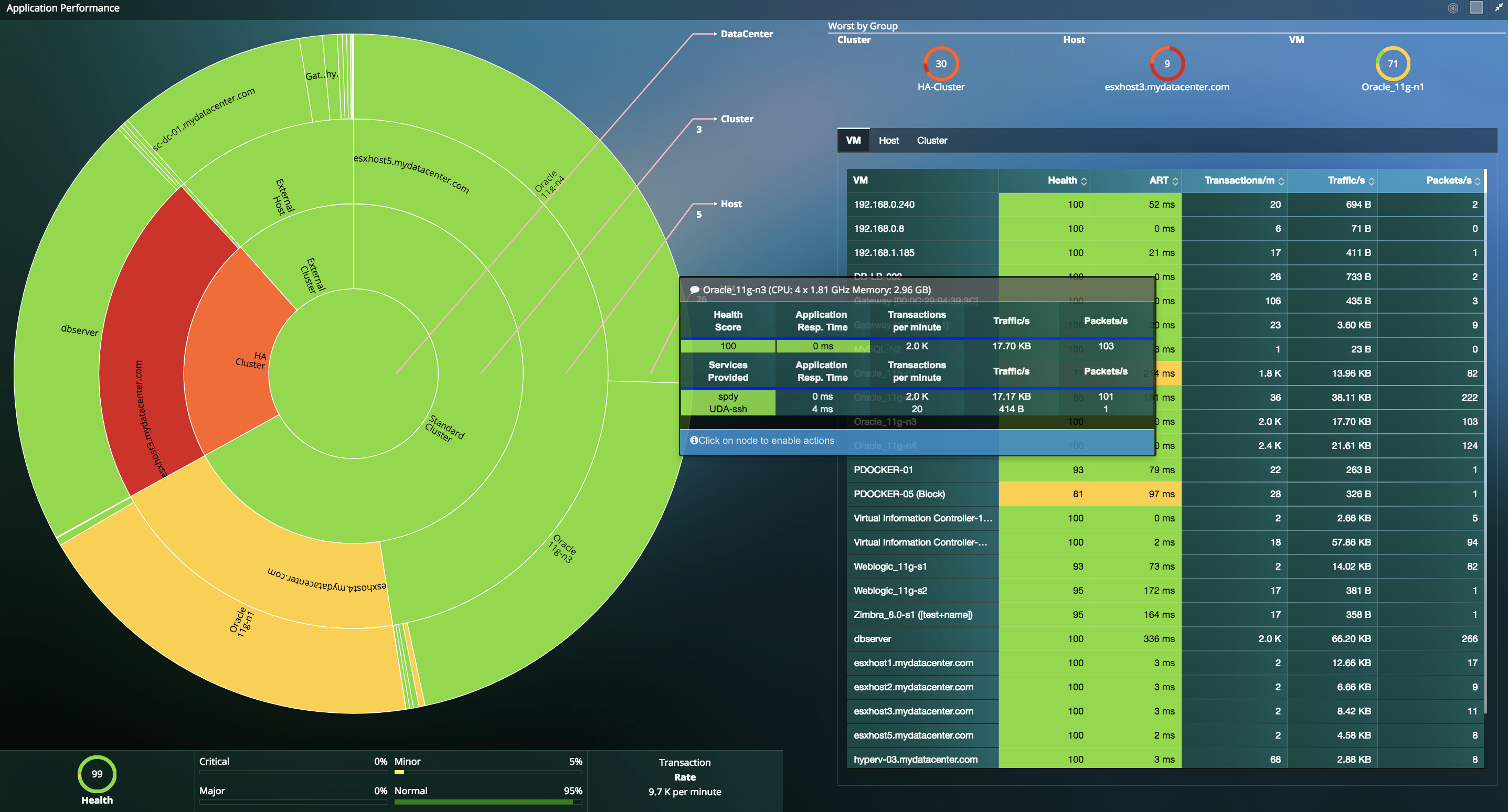
- Full stack visibility (Application Performance Monitoring, Infrastructure Performance Monitoring, Network Monitoring, Storage Monitoring) for virtualized data centers reduces troubleshooting time from days to minutes, enabling lean IT teams to get time back for more strategic projects
- Identify blind spots in the infrastructure, and eliminate finger pointing between infrastructure and application teams with automated root cause and forensics.
Read more about full-stack monitoring with Uila by clicking the button below:
Full-Stack Monitoring
Agentless & Seamless Discovery for over 4,200 applications, including EPIC, HL7 and DICOM
- Application auto-discovery for over 4,200 applications with deep packet inspection.
- Identify and solve EPIC, HL7 and DICOM issues, which may impact your patient admission systems, billing systems, etc.
- Review Application Response times, Transaction volume and Traffic volume for each individual application without interfering with their existing processes and services.
- Automated DPI to classify previously unknown traffic using embedded machine-learning algorithms.
- IT teams can identify blind spots in the infrastructure, and eliminate finger pointing between infrastructure and application teams with automated root cause and forensics.
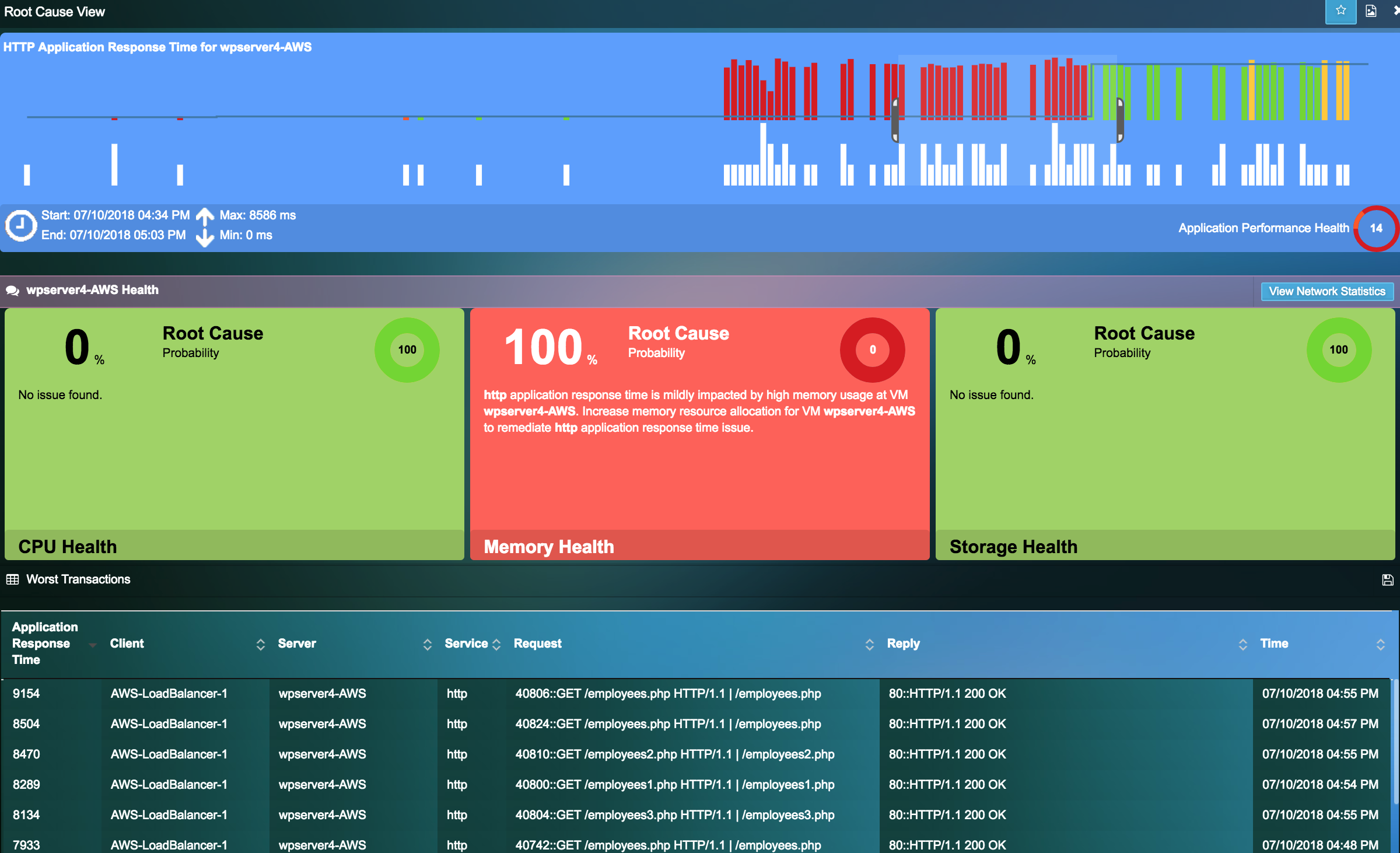
Troubleshoot at High Velocity with Root-Cause Analysis
- Monitor application performance and perform rapid root-cause analysis and reduce MTTR from days to minutes.
- Utilize continuous Machine Learning (ML) & Behavior Learning algorithms to identify anomalies from performance baselines instead of manual guesstimates, to provide unprecedented level of accuracy.
- Prevent alert storms and false positives with getting alerts only on issues that matter.
- No need to manually interpret issues from multiple sources. Let Uila do that for you.
- Real-time or time travel in the past to detect and solve intermittent issues.
Rapid Detection of Network Anomalies & Threats
- Real-time Full Network Security Insight with comprehensive Applications, Network and Infrastructure & East-West traffic statistics across VMs.
- Detect East-West traffic which may indicate that a malware penetrated the outer security perimeter and has launched further attacks inside a vulnerable data center.
- Identify Dormant VM vulnerabilities in your data center.
- Detect Abnormal patterns of connections and traffic flow indicating a network security threat that could impact business service performance and operations
- Packet Capture for Deep Packet Inspection & Forensic Evidence to solve network security challenges
- Ability to identify nearly all protocols and applications behind IP flows, on mobile and wireline networks, in any geography.
Resources
-
Uila Lightning Chat on Monitoring Healthcare environmentsLightning Chat by Dilip Advani, VP of Marketing on delivering service performance in Healthcare.
-
Success Story: Healthcare organization resolves critical Patient Care Application errors in minutesSuccess Story on a Healthcare organization that resolved database errors for their patient care application in minutes.
-
Hospital Group saves $500K based on Rightsizing Guidance from UilaUS-based Hospital Group saves $500K based on Rightsizing Guidance from Uila for their Epic EMR Database.
-
Healthcare Facility & Services Group solved slow Remote Access issuesUS State operated Healthcare Facility & Services Group solved slow Remote Access issues using Uila.
-
Uila Proves Critical to Lake EMS Virtual Data Center VisibilityUila’s Solution becomes critical tool for data center visibility and rapid application root cause analysis.
-
Large Hospital Success StoryUila Success Story on how a large hospital solved the challenge of email outages due to poor transfer of knowledge to a new IT employee.
Ready to begin your Monitoring Journey with Uila?
Start a 21-day Free Trial Now
Request Trial


.png)
.png)



