Challenges with the changing Cyber Threat Landscape
-
Most enterprise organizations have also learnt that preventive security methods are not able to block all cyber attacks, so it has become critical for SecOps teams to prevent that network intrusion from becoming a data/financial/reputation loss. Advanced cyber threats like Ransomware these days easily penetrate the deployed perimeter-firewall and work around the host-based security solutions to move laterally through the Data Center or Cloud deployment in stealth mode. Organizations traditionally have done a poor job in that area of identifying the lateral east-west movement of traffic in the environment, and often have no correlation of the threats back to their mission critical applications, thus leaving security teams struggling with prioritizing their efforts.
- Alert Fatigue trying to figure out what threats are real and need to be immediately dealt with
- Bogged down by day to day management tasks
- Too much time and effort spent in documentation and reporting, instead of focusing on solving the problem
- Working late hours, as current monitoring techniques and tools are not efficient
- Co-ordinating (Finger-pointing actually!) with IT Operations teams due to inconsistent visibility
- Not seeing career growth or involvement with the organization's strategic initiatives
- Focus on alerts that are impacting the business-critical application
- Reduce the Mean Time to Identification of the threats
- Provide a correlated view for all teams within the IT organization (NetOps, SecOps, ITOps, DevOps) to figure out the root cause behind the application outage or slowdown and eliminate expensive and stressful war room conversations and avoid being the "fall guy or girl".
The most commmon pain points for Security Engineers include:
These pain-points can be eliminated by practices and tools that help your security team:
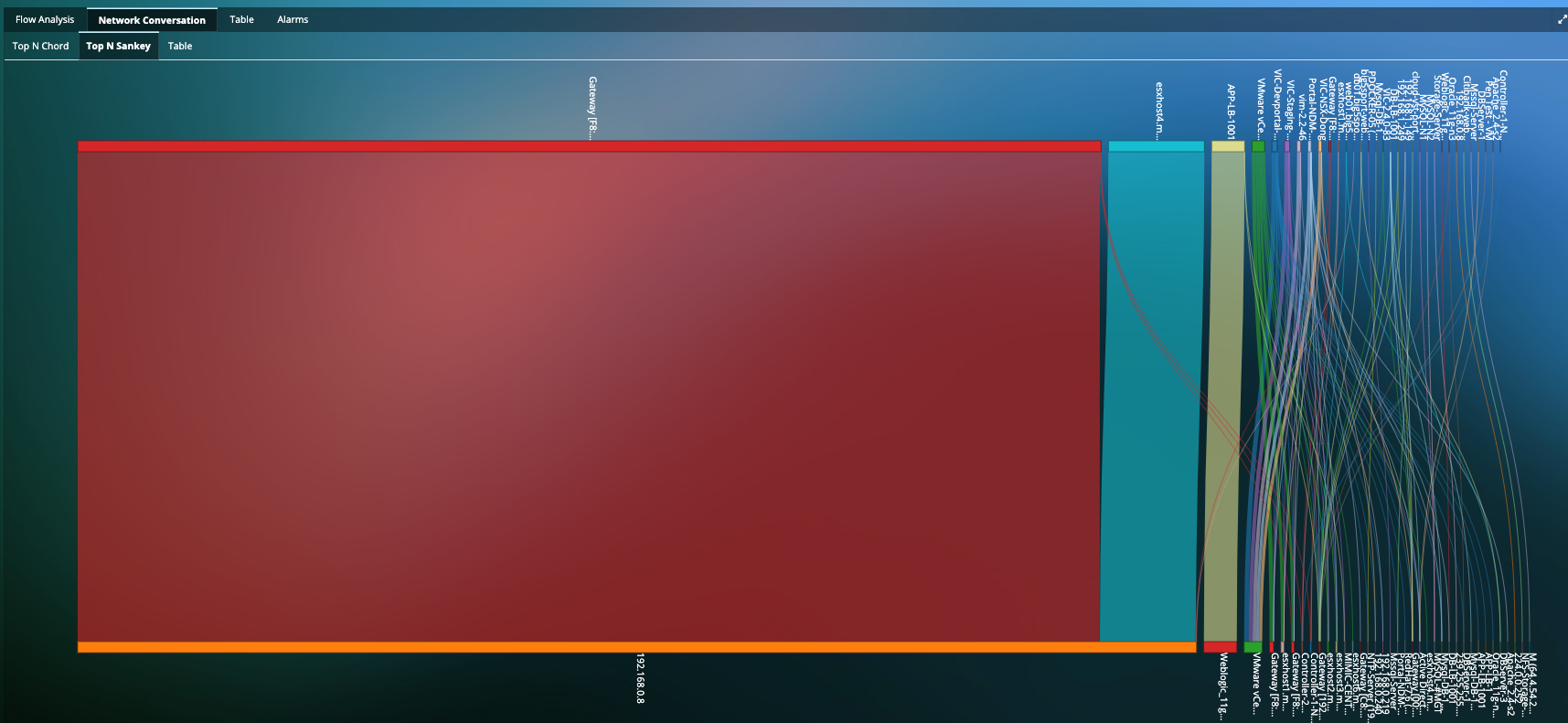
Monitor Lateral Movement of Authorized and Unauthorized Traffic
- Deep visualization of a clear indicator of a threat that is attempting to extend its reach into the network.
- Monitor attackers pivoting between compromised hosts to bounce deeper into the network.
- Network Traffic Insights into Network Traffic, Network Response Time, Fatal retries, Resets, Zero Window, etc.
- Application-centric visualization for traffic between servers to provide insight into applications being compromised, or used to compromise.
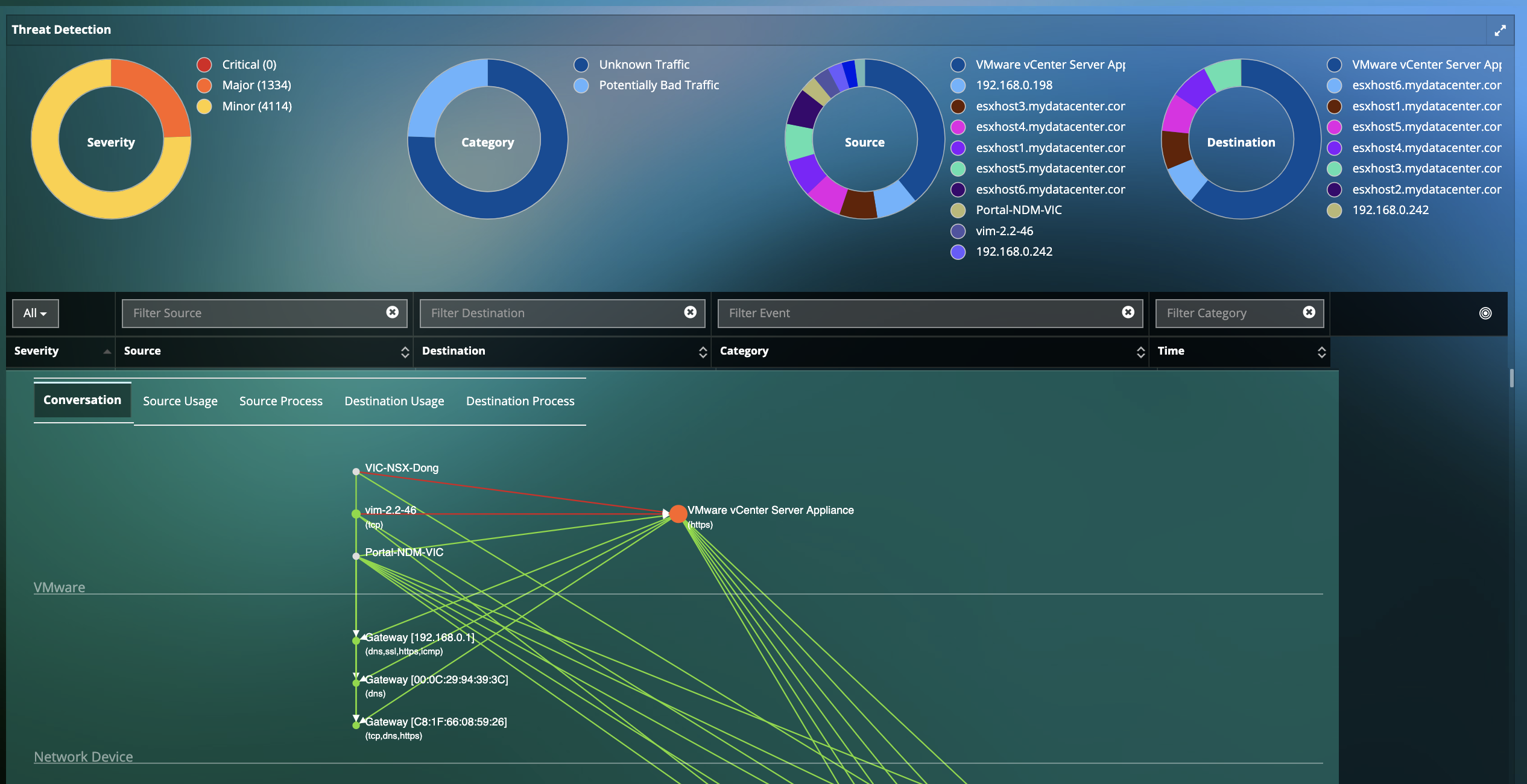
Proactively Detect Advanced Malicious Threats in Real-Time for Data Center and Cloud Workloads
- Real-time Detection for thousands of Advanced and Persistent threats including Malware, Exploit Kits, Webshells, Port Scans, SMB Probes, Information Leakages, Obfuscation, OS fingerprinting, and many more. :
- Deep Infrastructure & Application Insights into Current as well as Potential Compromised Assets.
- Reduce Risk associated with outbound connections with immediate visibility into Traffic Exfiltration from your deployment to unauthorized or malicious locations directly on a world map.
- Prioritize your efforts with visibility into the Top Exploited Hosts.
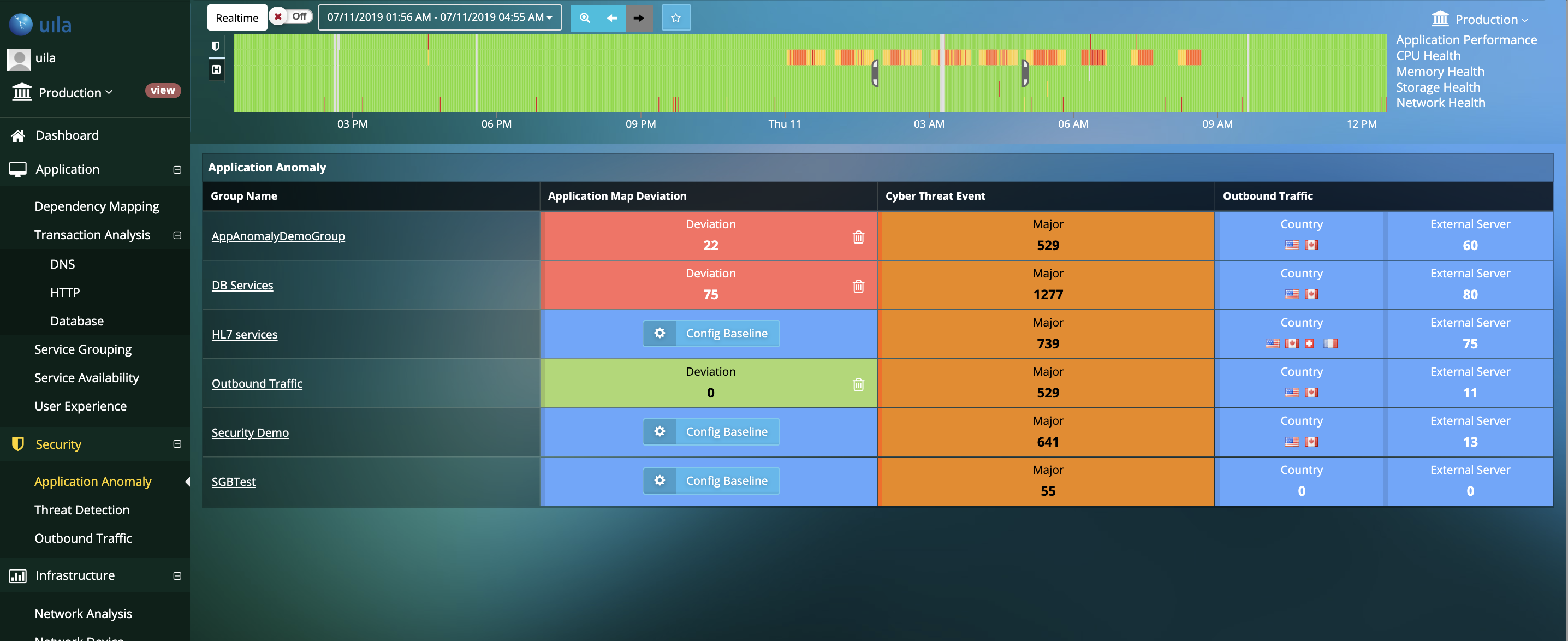
Visualize Application Behavior Deviation from Corporate Security Policy
- Identify anomalies in application behavior that may occur before, during or as a follow up after a successful attack
- Insights into deviations such as unauthorized dependency changes, new applications/services/protocols running on the VMs, additions of unauthorized VMs or tearing down of your mission critical VMs, and others.
- Map thousands of cyber threats directly to the anomalous behavior in application performance and dependencies to identify root-cause.
Resources
-
Cyber Threat Monitoring for the Hybrid EnterpriseQuick 3 minute video that talks about the changing Threat Landscape with attacks moving laterally within the Data Center and Cloud deployments, the importance of identifying Application Anomalous Behavior and Data exfiltration activities and finally on how you can protect your mission critical application workloads with Uila.
-
Application Behavior Anomaly Detection with UilaQuick video on how Uila can identify anomalies in application behavior that may occur before, during or as a follow up after a successful attack.
-
Cyber Threat Detection with UilaQuick video on how Uila can identify advanced cyber threats in your deployment.
-
Lateral Traffic Movement Analysis with UilaQuick video on how Uila can monitor authorized and unauthorized lateral movement or east-west traffic movements within your deployment.
-
Data Exfiltration Analysis with UilaQuick video on how Uila can monitor for outbound traffic from your data center resources to the Internet, that could indicate Data Exfiltration as well as certain Command and Control events.
-
Uila's DPI Methods for Detecting Lateral MovementQuick overview on Uila's DPI methods for lateral movement detection.
-
Uila for Webshell Threat DetectionQuick brochure on how to use Uila for Webshell Threat Detection.
-
Uila for Cyber Threat Monitoring Solution BriefQuick solution brief on Uila's Application-centric approach to cyber threat monitoring.
-
Security Analytics and Change Control in the Modern Data Center White PaperRead this white paper to get insights into the security and change control issues of the Modern Data Center.
-
Data Center Security ChallengesIn this blog, we talk about the four critical security challenges IT teams face in any data center.
-
Shadow IT challenge? Take back controlIn this blog we talk about Shadow IT and how organizations can take back control of their own environment and destiny.
-
Wine Producer Success StoryUila Success Story on how a large wine producer solved their Shadow IT challenges.
Ready to begin your Monitoring Journey with Uila?
Start a 21-day Free Trial Now
Request Trial