Eliminate Shadow IT, Stay on Top of Changes & Stay in Alignment with Organization’s Business Objectives
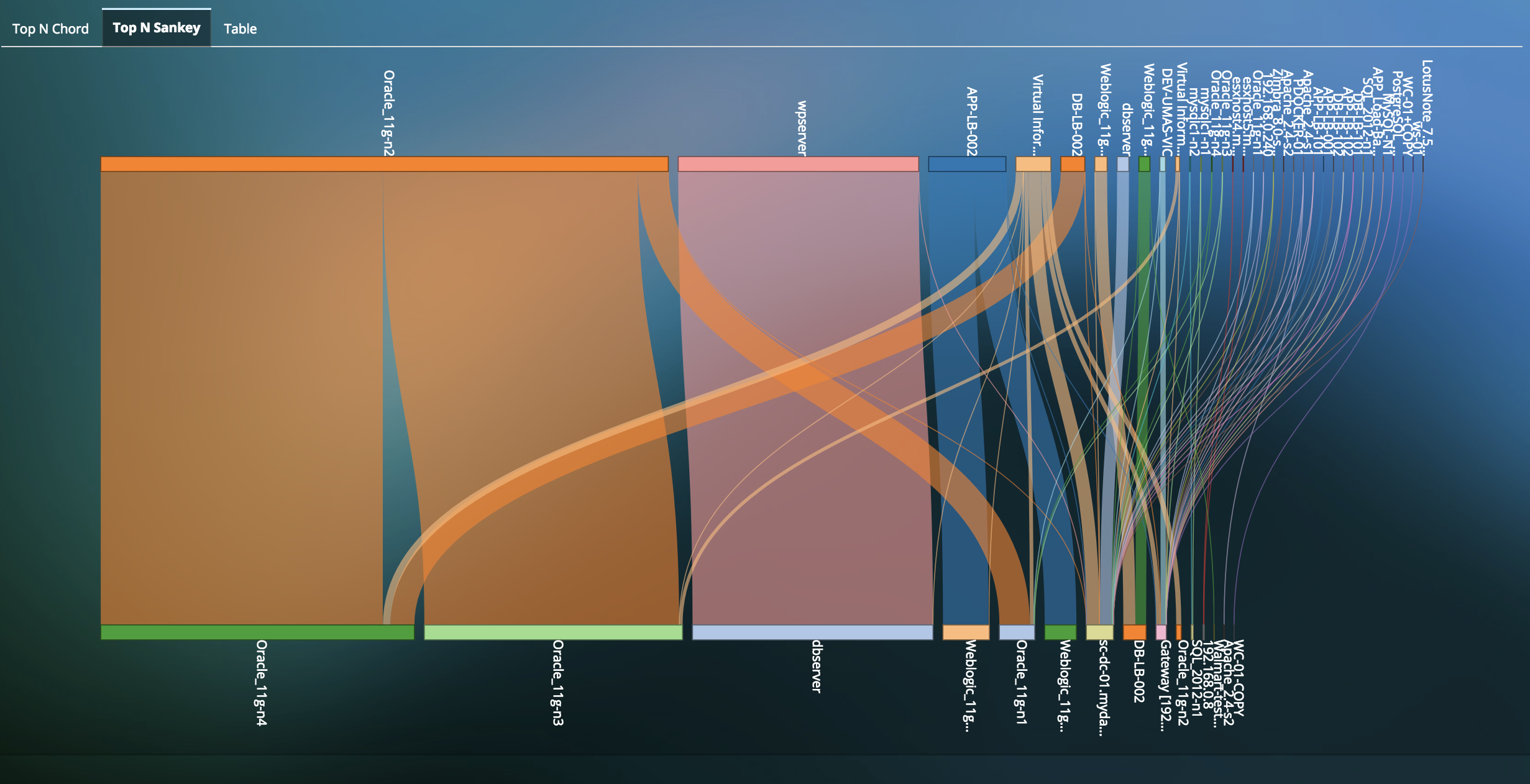
- Support Change Management to manage the unpredictable evolution of IT workloads, networks and technologies
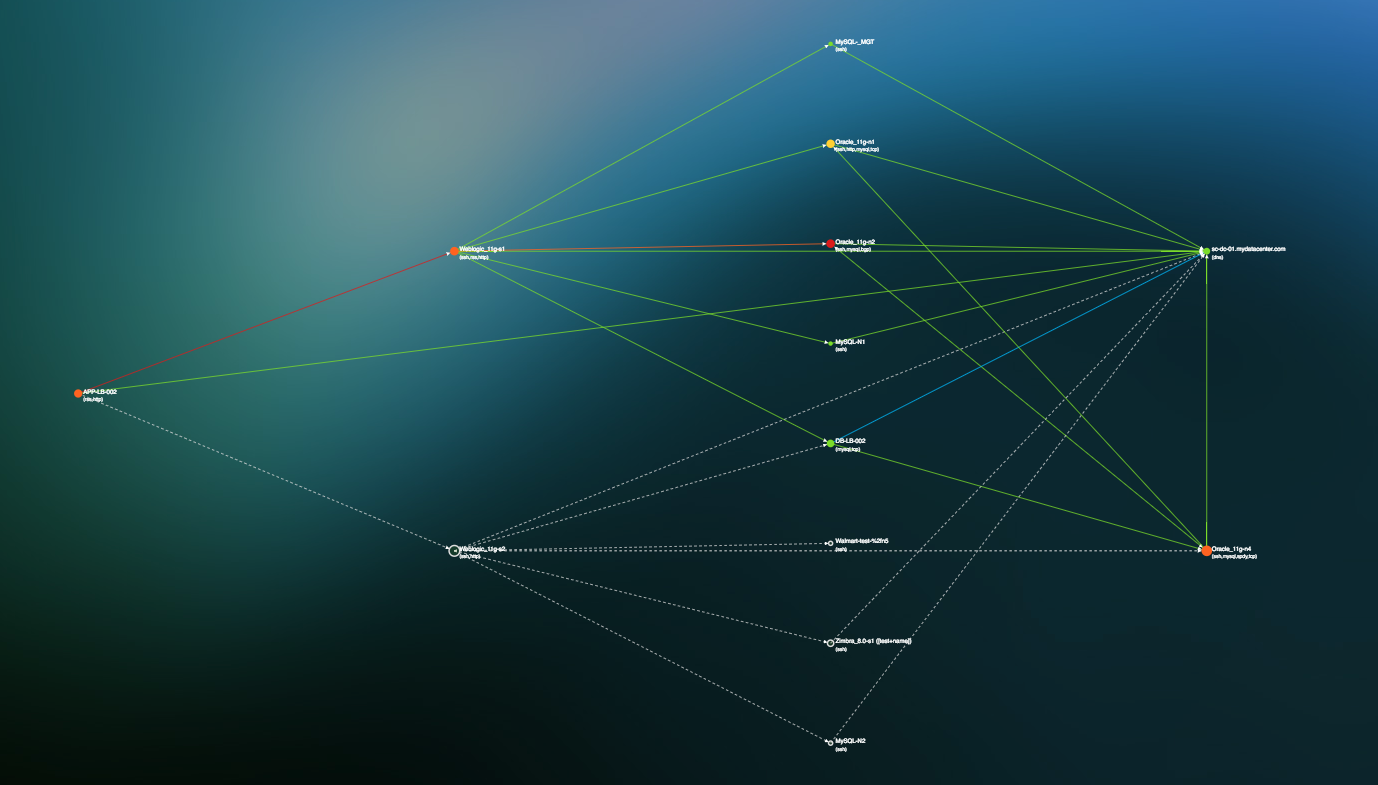
- Help IT staff to accurately find, follow and fix any part of the infrastructure
- Get Alerted to, if not completely prevent Shadow IT (roll out of new applications or even Servers) or missing resources within your organization
- Insights into misconfigurations of infrastructure, network and applications
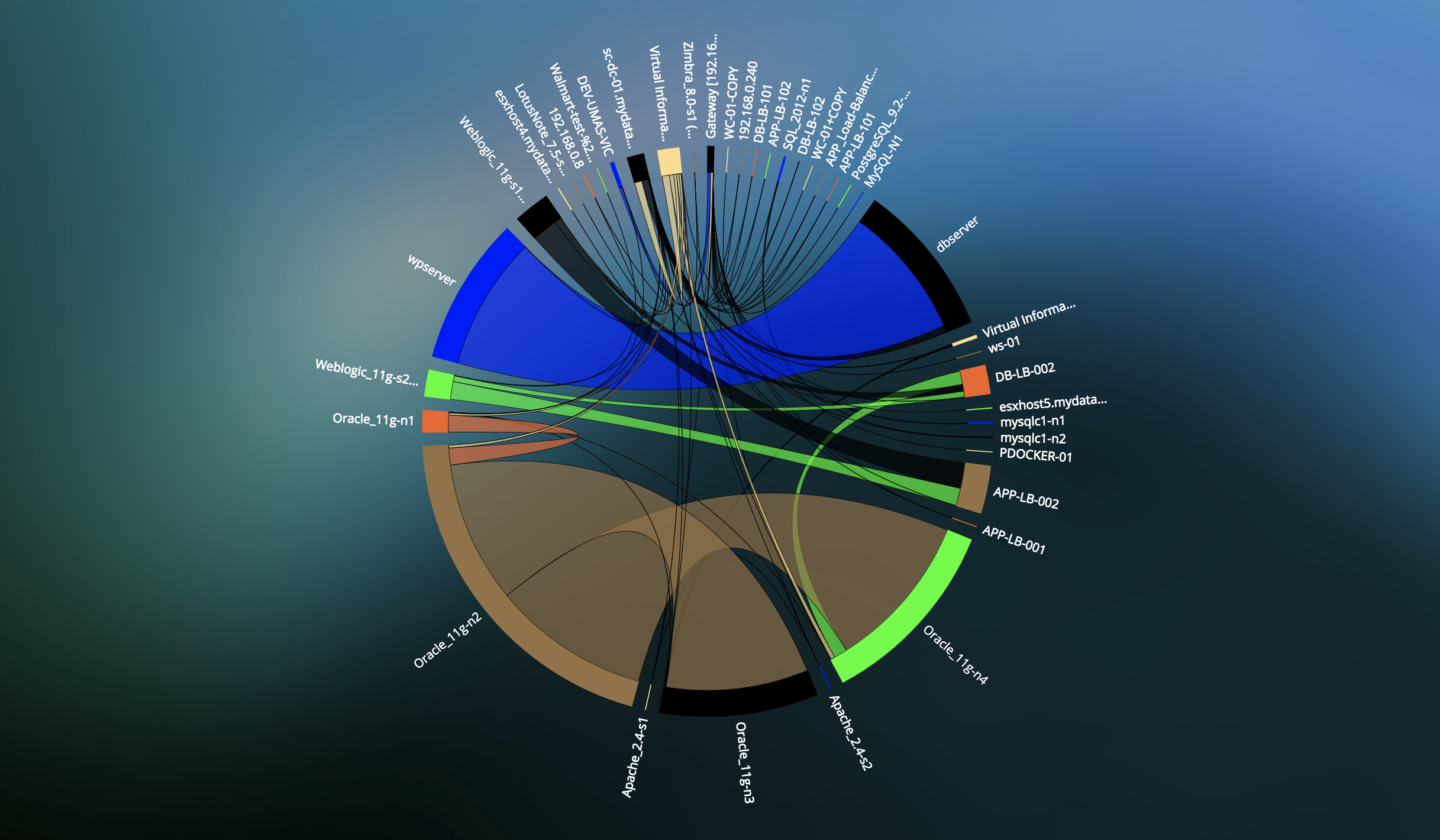
Rapid Detection of Network Anomalies & Threats
- Real-time Full Network Security Insight with comprehensive Applications, Network and Infrastructure & East-West traffic statistics across VMs.
- Detect East-West traffic which may indicate that a malware penetrated the outer security perimeter and has launched further attacks inside a vulnerable data center.
- Identify Dormant VM vulnerabilities in your data center.
- Detect Abnormal patterns of connections and traffic flow indicating a network security threat that could impact business service performance and operations
- Packet Capture for Deep Packet Inspection & Forensic Evidence to solve network security challenges
- Ability to identify nearly all protocols and applications behind IP flows, on mobile and wireline networks, in any geography.
Identify Policy Violations & Enforce Policy Compliance
- Support Change Management to manage the unpredictable evolution of IT workloads, networks and technologies and identify policy violations. Create baselines and visualize policy violations compromizing security and compliance for the environment.
- Quick visibility into disappearing assets and new unauthorized application connections or dependencies.
Resources
-
Network Security Analytics with UilaQuick product video on how to use Uila for Network Security Analytics.
-
Shadow IT challenge? Take back controlIn this blog we talk about Shadow IT and how organizations can take back control of their own environment and destiny.
-
Data Center Security ChallengesIn this blog, we talk about the four critical security challenges IT teams face in any data center.
-
Uila for Network Security AnalyticsQuick 2-page Solution brief on Uila for Network Security Analytics.
-
Change control monitoring with UilaQuick product video on how to use Uila for change control monitoring in applications and their dependencies in the modern data center.
-
Wine Producer Success StoryUila Success Story on how a large wine producer solved their Shadow IT challenges.
Ready to begin your Monitoring Journey with Uila?
Start a 30-day Free Trial Now
Request Trial